Configuring Azure Site-to-Site connectivity using VyOS Behind a NAT – Part 3
In this, part 3 of the series, we’ll implement the configuration required for VyOS to enable it to become a VPN endpoint with which we can connect to our Azure Virtual Network Gateway to form our Site-to-Site VPN.
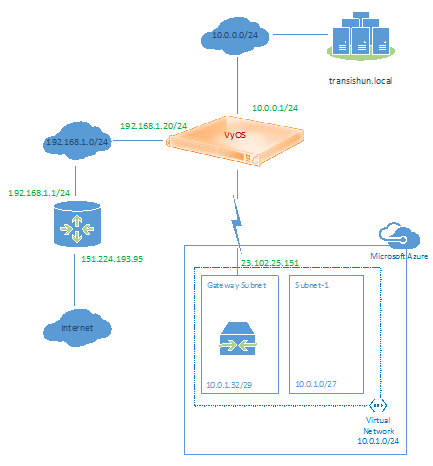
If you still haven’t, consider reading part 1 and part 2 of this series to provide the background of our modest network and how we configure Azure to create its side of the VPN cross-premises connection. As a reminder, our network configuration looks as follows (no tunnel and no Azure VM yet).
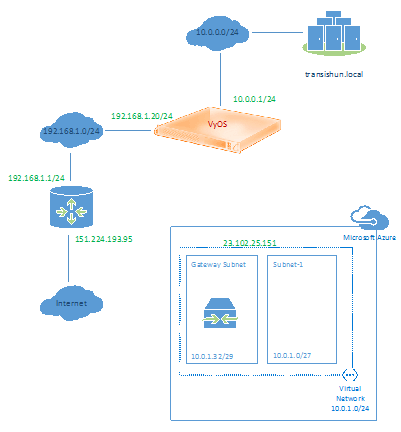
VyOS
Now, if you’ve arrived here expecting a rundown of what a Site-to-Site VPN connection is, IPSec, IKE/ISAKMP, AH, Phase 1, Diffie-Hellman, proposals etc. then you’re likely to be disappointed. There’s little point in me covering old ground re-explaining what is already covered very nicely by people far better qualified than I am. If you’re interested in reading about those subjects, obtain the Vyatta documentation (remember, VyOS is a fork of Vyatta!) on VPN and give it a read. This Rackspace website provides a link to the Vyatta 6.5R1 documentation.
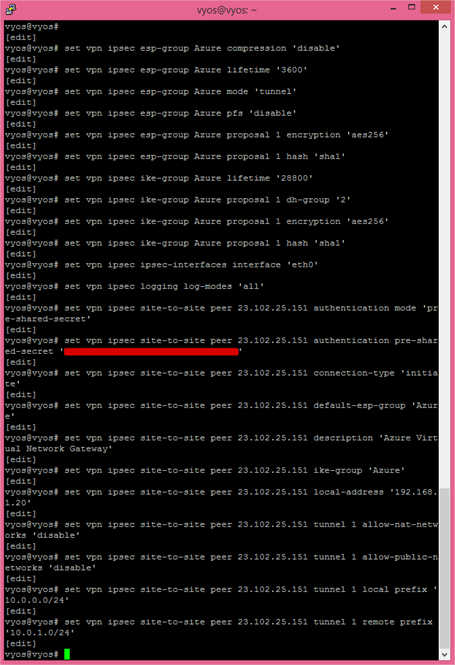
As mentioned, I’m not going to go over old ground but I will give you the required configuration commands to set up the Site-to-Site connection in VyOS. Of course, these commands are relevant to my local and the Azure virtual networks that I created in part 2 so should be adjusted. I’ve also called out where the Azure Virtual Network Gateway IP address (highlighted red) and Shared Key are used.
First, assuming you’ve installed and configured VyOS as per your own network – access it from the console or, if you’ve configured SSH access like I have, access it from there and enter configure mode.
Next we execute the following series of commands. Remember that you will need to edit the areas highlighted red
to include your Azure Network Gateway IP, shared key and appropriate other information such as the IP of the VyOS router and local and remote subnets. We obtained these during part 2 when the Virtual Network Gateway was created.
- set vpn ipsec esp-group Azure compression ‘disable’
- set vpn ipsec esp-group Azure lifetime ‘3600’
- set vpn ipsec esp-group Azure mode ‘tunnel’
- set vpn ipsec esp-group Azure pfs ‘disable’
- set vpn ipsec esp-group Azure proposal 1 encryption ‘aes256’
- set vpn ipsec esp-group Azure proposal 1 hash ‘sha1’
- set vpn ipsec ike-group Azure lifetime ‘28800’
- set vpn ipsec ike-group Azure proposal 1 dh-group ‘2’
- set vpn ipsec ike-group Azure proposal 1 encryption ‘aes256’
- set vpn ipsec ike-group Azure proposal 1 hash ‘sha1’
- set vpn ipsec ipsec-interfaces interface ‘eth0’
- set vpn ipsec logging log-modes ‘all’
- set vpn ipsec site-to-site peer 23.102.25.151 authentication mode ‘pre-shared-secret’
- set vpn ipsec site-to-site peer 23.102.25.151 authentication pre-shared-secret ‘[Azure Shared Key]‘
- set vpn ipsec site-to-site peer 23.102.25.151 connection-type ‘initiate’
- set vpn ipsec site-to-site peer 23.102.25.151 default-esp-group ‘Azure’
- set vpn ipsec site-to-site peer 23.102.25.151 description ‘Azure Virtual Network Gateway’
- set vpn ipsec site-to-site peer 23.102.25.151 ike-group ‘Azure’
- set vpn ipsec site-to-site peer 23.102.25.151 local-address ‘192.168.1.20‘
- set vpn ipsec site-to-site peer 23.102.25.151 tunnel 1 allow-nat-networks ‘disable’
- set vpn ipsec site-to-site peer 23.102.25.151 tunnel 1 allow-public-networks ‘disable’
- set vpn ipsec site-to-site peer 23.102.25.151 tunnel 1 local prefix ‘10.0.0.0/24‘
- set vpn ipsec site-to-site peer 23.102.25.151 tunnel 1 remote prefix ‘10.0.1.0/24‘
Once executed, the screen should look something like this.
Before the configuration will take, it must be committed. Type commit at the command line now then navigate to the Azure portal > Networks and open the dashboard for the Virtual Network.
Initially you’re likely to see the following image showing that the VPN is attempting to connect.

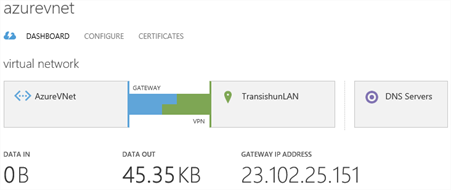
Now that the configuration is committed on your VyOS software router, assuming all of the pre-requisites as discussed in part 1 are in place, including appropriate port forwards in your edge router, the cross-premises Site-to-Site connection should form up and the Site-to-Site tunnel will connect, like so.
For completeness, I’ve included my VyOS router’s entire configuration below. Notice there is no NATing done anywhere.
firewall {
all-ping enable
}
interfaces {
ethernet eth0 {
address 192.168.1.20/24
description DMZ
duplex auto
hw-id xx:xx:xx:xx:xx:xx
smp_affinity auto
speed auto
}
ethernet eth1 {
address 10.0.0.1/24
description Internal
duplex auto
hw-id xx:xx:xx:xx:xx:xx
smp_affinity auto
speed auto
}
loopback lo {
}
}
protocols {
static {
route 0.0.0.0/0 {
next-hop 192.168.1.1 {
}
}
}
}
service {
dns {
forwarding {
cache-size 0
listen-on eth1
name-server 192.168.1.1
name-server 8.8.8.8
}
}
ssh {
port 22
}
}
system {
config-management {
commit-revisions 20
}
console {
device ttyS0 {
speed 9600
}
}
host-name vyos
login {
user vyos {
authentication {
encrypted-password xxxxxxxxxxxxxxxxxxxxxxxxxx
}
level admin
}
}
ntp {
server 0.pool.ntp.org {
}
server 1.pool.ntp.org {
}
server 2.pool.ntp.org {
}
}
package {
auto-sync 1
repository community {
components main
distribution helium
password ""
url http://packages.vyos.net/vyos
username ""
}
}
syslog {
global {
facility all {
level notice
}
facility protocols {
level debug
}
}
}
time-zone UTC
}
vpn {
ipsec {
esp-group Azure {
compression disable
lifetime 3600
mode tunnel
pfs disable
proposal 1 {
encryption aes256
hash sha1
}
}
ike-group Azure {
lifetime 28800
proposal 1 {
dh-group 2
encryption aes256
hash sha1
}
}
ipsec-interfaces {
interface eth0
}
logging {
log-modes all
}
site-to-site {
peer 23.102.25.151 {
authentication {
mode pre-shared-secret
pre-shared-secret xxxxxxxxxxxxxxxxxxxxxxx
}
connection-type initiate
default-esp-group Azure
description "Azure Virtual Network Gateway"
ike-group Azure
local-address 192.168.1.20
tunnel 1 {
allow-nat-networks disable
allow-public-networks disable
local {
prefix 10.0.0.0/24
}
remote {
prefix 10.0.1.0/24
}
}
}
}
}
}
Now that our Site-to-Site VPN is configured and connected, in the next post in this series I’ll create a Virtual Machine in the Azure Virtual Network, prove it has connectivity with my on-premises network and vice-versa as well as add it to my on-premises domain. I’ll also briefly discuss the process of adding a Domain Controller in Azure. Our network now looks as follows (no Azure VM yet):
-Lewis






